I wrote a message to the mailing list (google groups) with plain text format. The content was just one sentence and “thank you” as end.
google groups will forward the message to everybody in the list. When forwarding, google will does a SRS (sender rewrite). So SPF has no contribution to DMARC validation in recipients. In this case, I use another gmail as test recipient.
And, google modified the message body, adding a signature at end. See screenshot below. The green part is my original content. The red part is the signature adding by google. So DKIM will break in the recipients.
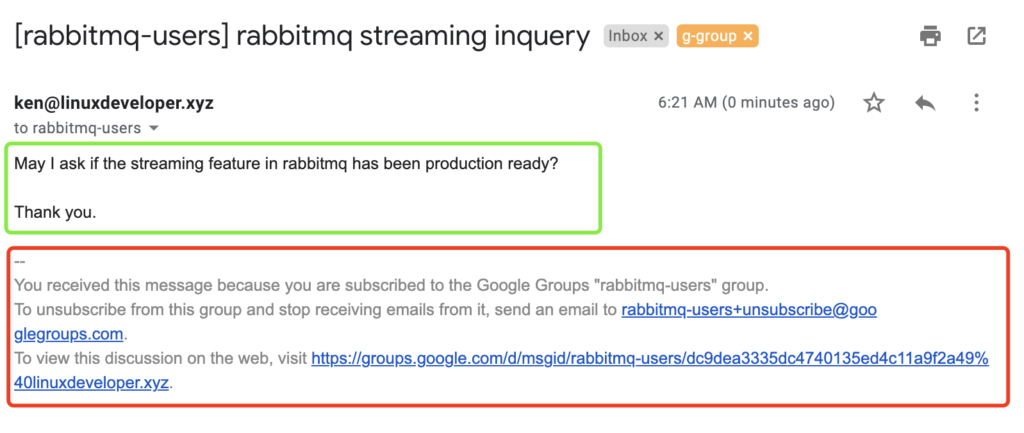
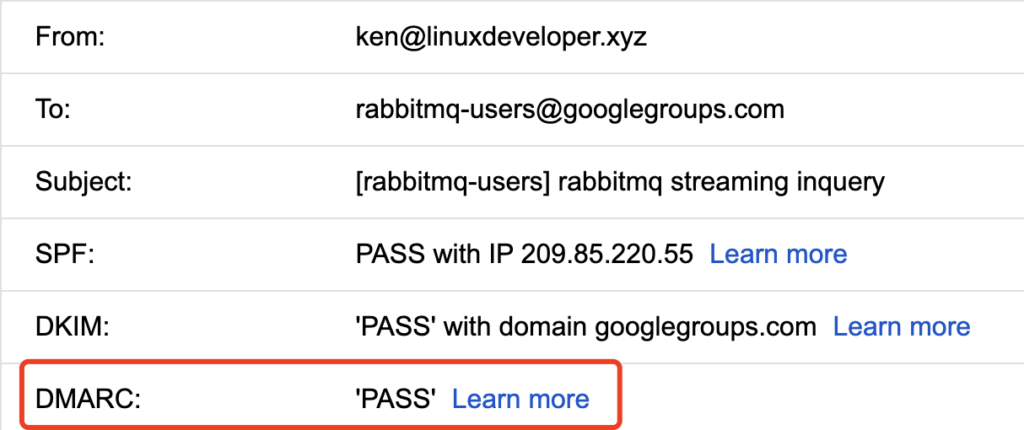
What strange is, this message was labeled by google as “DMARC PASS”, see screenshot below.
My SPF, DKIM, DMARC settings:
linuxdeveloper.xyz. 299 IN TXT "v=spf1 include:spf.migadu.com ?all"
_dmarc.linuxdeveloper.xyz. 299 IN TXT "v=DMARC1; p=none;"
key1._domainkey.linuxdeveloper.xyz. 299 IN CNAME key1.linuxdeveloper.xyz._domainkey.migadu.com.
key2._domainkey.linuxdeveloper.xyz. 299 IN CNAME key2.linuxdeveloper.xyz._domainkey.migadu.com.
key3._domainkey.linuxdeveloper.xyz. 299 IN CNAME key3.linuxdeveloper.xyz._domainkey.migadu.com.I can’t understand why this DMARC got passed by google. Both DKIM and SPF have no contribution to DMARC validation.
I asked this question on postfix’s mailing list. Thanks to our friend @Raf who gave the wonderful explanation. I quote his writing below.
Warning: This is just a theory, but it's the only
reasonable one I could think of.
Google is aware of the fragility of SPF/DKIM/DMARC when
it comes to mailing lists, which is why they use ARC:
Authenticated Received Chain (ARC) Protocol
https://tools.ietf.org/html/rfc8617 (Experimental)
ARC is a way for remailers to add an authenticated
chain of custody to an email, where they check
SPF/DKIM/DMARC when they receive the original email,
and then attest that each check passed or failed at
that time, and then they provide a DKIM-like signature
to prove that it was really them that made the
attestation.
If you look in the headers of a googlemail email,
you'll see these headers:
ARC-Seal
ARC-Message-Signature
ARC-Authentication-Results
There can be a set of these three headers for every
ARC-enabled remailer along the path. The googlegroups
email that I receive tends to have two sets, both added
as the mail passes between various google servers.
The ARC-Authentication-Results header contains the
SPF/DKIM/DMARC check results for the original mail, and
this gets copied up through the chain. The other two
headers in each set enable the receiver to check the
authenticity of its contents.
Gmail is probably checking the ARC chain and seeing
that DMARC was valid when googlegroups received the
original email, and that's what gmail is reporting to
you as a DMARC pass.
I'm not sure how much ARC is used. From my tiny
personal sample set, it's almost all Google and
Microsoft. So maybe that's a lot. And who checks it?
It's hard to tell. If gmail checks ARC but doesn't
mention it by name, perhaps other mail providers are
doing that too.
There is a milter for it called OpenARC, written by the
same group that wrote OpenDKIM and OpenDMARC, but it
seems to have been abandoned two years ago when it was
still in beta stage. And it doesn't get a mention in
the postfix setup tutorials that I've come across.
I can find people asking how to set it up, but not
so much in the way of satisfactory answers.
Without something like OpenARC, OpenDMARC is going to
produce lots of false positives because it doesn't know
to defer to ARC checking in the presence of ARC headers.
So ARC is probably needed for running the mailing lists. I will check them soon.
